Digital injection attacks pose a highly sophisticated and growing threat to the security of biometric systems.
From authentication on mobile devices to identity verification in banks and government services, biometric solutions offer an unprecedented combination of security and convenience that has driven their adoption in numerous identity verification projects.
However, as the implementation and use of these technologies have increased, so too have the associated threats. One of the most significant risks facing a system that uses biometrics is digital injection attacks. In these attacks, cybercriminals use advanced techniques to impersonate legitimate users and gain unauthorised access to their accounts and systems.
What are digital injection attacks?
Digital injection attacks refer to the technique of inserting or injecting biometric data into a biometric verification or authentication system to impersonate someone else, deceive the system, and gain unauthorised access.
These attacks can take various forms, with the injected information being either real or synthetic images, such as deepfakes.
Typically, the injection occurs at the data capture stage or by directly intercepting the communication channel. Hackers often bypass the camera, microphone, or biometric sensor of a device to inject false biometric data.
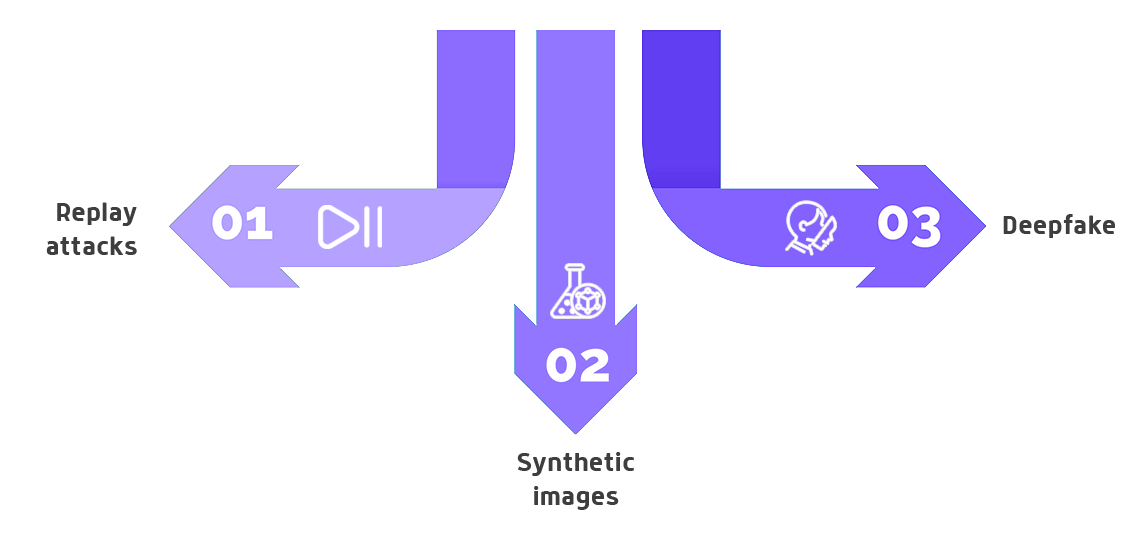
These attacks can be classified into several categories, each with its own techniques and specific objectives.
- Replay attacks. Replay attacks involve capturing valid biometric data from a person and reusing it to access authentication systems by impersonating that person. For example, an attacker might intercept a transmission of legitimate biometric data, such as a video recording of the target, and replay it during the authentication process to deceive the system. If the attack involves presenting the recording via a tablet or mobile device, it is considered a presentation attack. When the recording is injected directly into the application, it is classified as a digital injection attack.
- Synthetic images. Using advanced software, attackers can create fake images that mimic the biometric features of a real person or create an entirely new fake identity. These synthetic images can be photos, videos, or even three-dimensional models designed to resemble the legitimate user, enabling the creation of various synthetic identities.
- Deepfakes. Leveraging artificial intelligence technologies, deepfakes are hyper-realistic videos or images depicting a real person doing or saying things they never actually did. In the context of biometrics, deepfakes can be used to deceive facial recognition or voice recognition systems (known as voice deepfakes). With deepfake video injection, an attacker impersonates another person during the authentication process, fooling facial recognition systems.
Attacks on communication and capture channels often target the camera capturing the facial image, deceiving the system through a virtual camera that injects images or videos, or even the server-side API by exploiting vulnerabilities to inject false data.
Another fraud technique used in other digital domains that can be employed to inject false biometric data is the famous man-in-the-middle attack. In this scenario, the attacker acts as a proxy between the user attempting to verify their identity and the biometric verification system, injecting false biometric data in the process.
The impact of these attacks on the security of a biometric system is significant. A successful attack not only compromises the system’s security but can also lead to identity theft, financial fraud, and a loss of trust in biometric technologies.
To achieve the highest level of security in our biometric system, it is ideal to use multiple complementary strategies that strengthen our protection against biometric injection attacks.
How digital injection attacks work
Imagine you have a secure bank account protected by an advanced facial recognition system. But what if a cybercriminal manages to fool the system with a fake image or video? This is precisely what happens in a biometric injection attack.
Instead of trying to deceive the system with a mask or a photo (a presentation attack), criminals use generative artificial intelligence to create fake biometric evidence. This evidence is “injected” into the security system, making it believe that it is dealing with a real person.
The injected data can be generated using artificial intelligence and machine learning, making it increasingly realistic and difficult to detect.
For example, an attacker could create a synthetic image of a person using a deepfake and then inject that image into a facial recognition system to gain unauthorised access in that person’s name.
Similarly, the attacker could create a fake digital identity and use it to authenticate themselves in an authentication system.
![]() Mobbeel’s AI-based technology has been trained to detect various identity spoofing threats, including presentation attacks, injection attacks, or manipulations of identity documents.
Mobbeel’s AI-based technology has been trained to detect various identity spoofing threats, including presentation attacks, injection attacks, or manipulations of identity documents.
Our identity proofing solution, MobbScan, has been certified and included in the Catalog of Products and Services of Security of Information and Communication Technologies (CPSTIC), confirming its compliance with the highest security requirements set by the National Cryptologic Center (CCN) in the HIGH category of the National Security Scheme (ENS).
Impact of injection attacks on biometric security
Digital injection attacks can have severe consequences for the integrity and security of biometric systems. These attacks exploit inherent vulnerabilities in the biometric verification process, where the authenticity of biometric data is crucial.
Vulnerabilities in biometric verification systems
- Quality of biometric data: Biometric systems rely on the quality and accuracy of captured biometric data. Low-resolution images, poor lighting, or noise in the data can make the system more susceptible to attacks.
- Data transmission: The transmission of biometric data between devices and servers can be intercepted by attackers. Without adequate encryption measures, this data can be captured and reused in replay attacks.
- Data storage: Biometric data stored in databases is also a prime target. If this data is not properly protected, attackers can access it and use it to impersonate identities.
- Social engineering: Attackers can use social engineering techniques to deceive users into providing their biometric data. This might include the use of deepfakes to trick people into giving away their authentication details.
Consequences of a successful injection attack
- Unauthorised access: Attackers can gain unauthorised access to systems and accounts protected by biometric authentication. This can include bank accounts, government systems, and sensitive personal data.
- Identity theft: Impersonation through stolen biometric data can lead to identity theft, where criminals can conduct fraudulent transactions, open accounts under false names, and cause significant financial and reputational damage.
- Financial fraud: Financial systems using biometric authentication are particularly vulnerable to injection attacks. Criminals can perform fraudulent transfers, make unauthorised purchases, and compromise the financial integrity of individuals and businesses.
- Loss of trust: Successful attacks on biometric systems can erode user trust in these technologies. This can result in slower adoption of biometric technologies and increased reliance on less secure authentication methods.
How to defend against digital injection attacks
Para mitigar los riesgos asociados con los ataques de inyección digital, es crucial tener un enfoque más amplio, teniendo en cuenta múltiples aspectos de seguridad, para implementar una combinación de técnicas de detección y prevención, que permitan detectar los ataques de inyección digital. Algunos métodos de defensa contra los ataques de inyección digital son:
Liveness detection
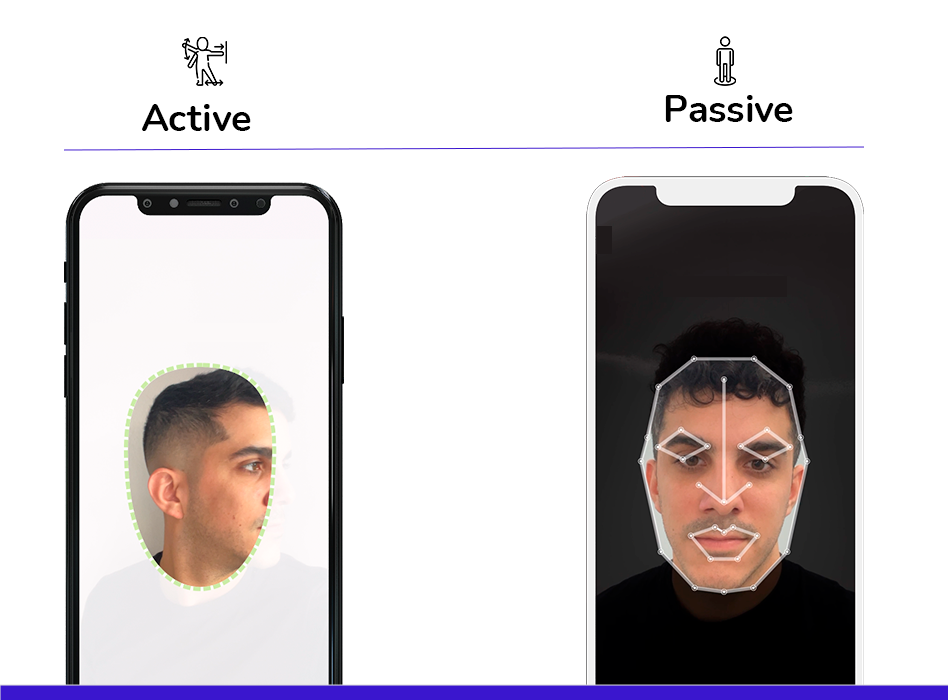
Liveness detection is essential for ensuring that biometric data comes from a legitimate source rather than an attempt at impersonation. This technique verifies that a real person is present in front of the camera, microphone, or biometric sensor. There are two main types of liveness detection:
- Active liveness detection: Active liveness detection requires user cooperation. The user must perform specific actions, such as blinking, smiling, or moving their head. These actions are challenging to replicate with photos or videos, making it difficult for attackers to bypass this security measure. However, this method can sometimes be cumbersome as users need to precisely understand and execute the required movements.
- Passive liveness detection: Passive liveness detection does not require any active participation from the user. Instead, it analyses characteristics like light reflections on the skin, skin texture, and micro-movements to verify the authenticity of the source. This method enhances user experience by reducing friction during the authentication process.
At Mobbeel, we prioritise passive liveness detection to improve usability. Our experience with active liveness detection showed that users often struggled to perform the required gestures correctly, leading to usability challenges and lower conversion rates. Therefore, despite having active liveness detection technologies, we developed our own passive liveness detection technology to ensure a seamless user experience.
Behavioural analysis
Behavioural analysis complements biometric authentication by monitoring user behaviour patterns. This can include observing how a user interacts with a device, their typing speed, and cursor movements. Significant deviations from usual patterns can indicate an impersonation attempt. For example, if a user typically types quickly but suddenly inputs data very slowly, this could trigger an alert for further verification.
Data encryption
End-to-end encryption of biometric data during transmission and storage is fundamental. Encrypting data ensures that even if intercepted, it cannot be used without the appropriate decryption keys. Using secure protocols like TLS (Transport Layer Security) for data transmission and performing integrity checks during the transmission processes are essential practices.
Mobbeel is ISO 27001 certified, ensuring that we implement, maintain, and continuously improve our Information Security Management System (ISMS). Additionally, we hold various certifications related to the security, efficacy, and performance of our technology, underscoring our commitment to robust data protection.

Multi-Biometric solutions
Multi-biometric solutions use more than one type of biometric data to authenticate a user. For instance, combining facial and voice recognition can significantly enhance security compared to using a single authentication method. This redundancy makes it more challenging for attackers to spoof multiple biometric traits simultaneously.
In addition to biometrics, incorporating other factors like tokens or passwords can further fortify security. For example, a user might be required to provide a fingerprint and a one-time password (OTP) sent to their mobile device.
Recommended tools and technologies
-
Liveness detection software: Tools that offer both active and passive liveness detection, such as Mobbeel’s fraud detection module, can effectively prevent impersonation attempts.
- Comprehensive biometric security platforms: Solutions like MobbID combine multiple biometric authentication methods with advanced security capabilities, offering robust protection against various attack vectors.
- Advanced encryption techniques: Employing robust encryption standards and secure key management technologies ensures that biometric data remains protected during transmission and storage.
By integrating these strategies, we can create a robust defence against digital injection attacks, safeguarding biometric systems from unauthorised access and ensuring user trust in biometric technologies.
Best practices for protecting biometric verification systems
As previously discussed, it is essential to adopt a comprehensive approach that not only implements methods to detect attacks but also prevents them. Here are a series of best practices to reinforce the protection of biometric systems:
- Security sistem design: Implement security principles from the outset in the system design, and regularly conduct risk assessments and penetration tests.
- Multi-Factor authentication (MFA): Combine biometrics with other authentication factors such as passwords or security tokens, ensuring that at least one factor is resistant to impersonation attempts.
- Security policies and protocols: Develop and maintain clear and up-to-date security policies, and establish protocols for rapid response to security incidents.
- Training and swareness: Train users and administrators on security threats and best practices for mitigating them. Additionally, promote a security culture within the organisation.
- Continuous Monitoring: Implement monitoring systems to detect and respond to suspicious activities in real-time and use behavioural analysis to identify anomalous patterns.
How Mobbeel can help
Dealing with injection attacks requires a multi-faceted strategy. At Mobbeel, we address injection attacks through multiple approaches. Our system is designed to analyze the video stream, distinguishing between Mobbeel’s video capture element and virtual camera sources.
Furthermore, our PAD (Presentation Attack Detection) technology is trained to identify deepfakes, a common component in both pre-recorded and real-time video injection scenarios.
Contact us if you want to use cutting-edge AI technology to prevent injection attacks and verify your users.

I’m a Software Engineer with a passion for Marketing, Communication, and helping companies expand internationally—areas I’m currently focused on as CMO at Mobbeel. I’m a mix of many things, some good, some not so much… perfectly imperfect.

GUIDE
Identify your users through their face
In this analogue-digital duality, one of the processes that remains essential for ensuring security is identity verification through facial recognition. The face, being the mirror of the soul, provides a unique defence against fraud, adding reliability to the identification process.




