Over the past decade, we’ve experienced an unprecedented digital revolution that has brought numerous benefits to both society and the European economy. It has facilitated trade, remote service delivery, and the creation of new market niches and business opportunities. The pandemic further highlighted the importance of well-regulated and standardized remote identification processes, as well as digital identities trusted by both public and private organizations. These aspects are also emphasized in the planned review of the eIDAS regulation (eIDAS 2.0), which will provide EU citizens with secure and transparent access to a new generation of electronic services, including the EU Digital Identity Wallet (EUDIW).
Remote Identity Proofing (RIDP) is a key function for most services envisaged in this context, thus intensifying the need for secure remote identity verification services that can be deployed quickly, at scale, and cost-effectively. This is because it is a key enabler for electronic transactions in the Digital Single Market.
However, the emergence of increasingly sophisticated cyber-attacks raises concerns about the reliability of the technology behind RIDP processes, pushing us to improve in areas such as awareness, risk analysis, and the development of robust countermeasures.
Through this article, we aim to provide professionals in the field with an updated insight into best practices for strengthening the security of remote identity verification methods, crucial for safely driving the European digital transformation.
To do this, we will analyze the recent best practices report regarding the Identity Proofing process published by ENISA, the European Agency for Cybersecurity.
Report on good practices for identity verification control
The main drivers behind ENISA’s creation of this report are the emergence of new threats and identity spoofing attacks, which breed distrust and concern regarding the reliability of identity verification technologies, as well as the request from various interested organizations and companies for information and guidance on implementing best practices in the use and implementation of these technologies.
Therefore, with this report, ENISA aims to achieve the following strategic objectives in the field of trusted services and electronic identification:
- Increase awareness among the various stakeholders involved.
- Assist in risk analysis practices, given the changing threat landscape in identity verification.
- Contribute to the development of robust countermeasures, enhancing the trust and reliability of remote identity verification methods (RIDP).
Evolution of Remote IDentity Proofing processes (RIDP)
Regarding RIDP methods (remote identity verification), it’s important to note that not all offer the same level of security and trust. Some rely solely on verifying identity documents, while others include capturing and validating user biometric data. This has direct implications for the level of assurance they can provide.
For example, methods solely based on capturing and validating identity documents may be susceptible to attack instruments such as forgery or manipulation of these documents, both physically and digitally.
In contrast, methods incorporating user biometric verification, such as capturing the face for facial recognition, offer a higher level of assurance by being able to more confidently link digital identity with the real identity of a physical person.
Furthermore, these developments are particularly relevant in the context of eIDAS 2.0 and the introduction of the EU Digital Identity Wallet (EUDIW), as the cases requiring identity verification with a high level of security will significantly increase.
Additionally, standardization bodies such as CEN, ETSI, and ISO are developing standards and technical requirements related to biometric security, presentation attack detection (PAD) testing, and remote identity verification methods. These efforts will contribute to establishing a common and coherent framework at the European level to address the security challenges posed by RIDP.
Summary of remote identity verification methods
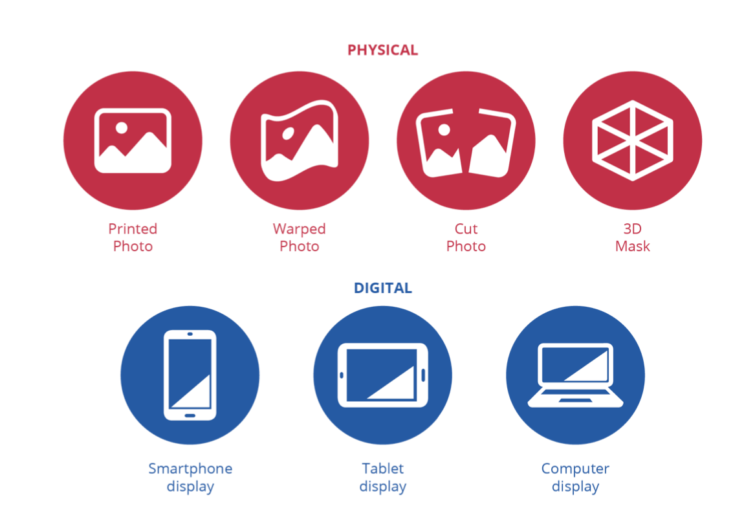
Emerging threats to Remote IDentity Verification (RIDP)
Two categories of attacks stand out for their relevance and difficulty of detection: presentation attacks and injection attacks, targeting both the subject’s face and identity documents.
Presentation Attack Detection (PAD)
Presentation Attack Detection involves the combination of software and/or hardware methods enabling a biometric system to detect attempts of identity spoofing during the biometric data capture phase.
Injection Attack Detection (IAD)
Injection Attack Presentation involves the combination of software and/or hardware methods enabling a biometric system to detect attempts of identity spoofing immediately after biometric capture.
Injection attacks against the face focus on identity spoofing through the injection of false biometric data during live capture. Instruments such as modified cameras, video playback devices, and deepfake software come into play here. Attack methods encompass injecting this data through APIs, in real-time, or asynchronously.
Attacks on Identity Documents
Concerning attacks on identity documents, attempts to forge or manipulate the data contained in these documents are examined, whether physically (e.g., altering real documents) or digitally (e.g., identity spoofing through synthetic documents: synthetic identity fraud).
A key aspect emphasized is the growing availability of tools and computational resources that enable the scaling and automation of such attacks, posing an increasingly significant risk to the reliability of RIDP processes.
Given this constantly evolving threat landscape, it is crucial for remote identity verification service providers to implement a set of robust best practices to effectively mitigate these risks.
![]()
Mobbeel’s AI-based technology has been trained to detect various identity spoofing threats, including presentation attacks, injection attacks, or manipulations of identity documents.
Our identity proofing solution, MobbScan, has been certified and included in the Catalog of Products and Services of Security of Information and Communication Technologies (CPSTIC), confirming its compliance with the highest security requirements set by the National Cryptologic Center (CCN) in the HIGH category of the National Security Scheme (ENS).
Good practices for reinforcing RIDP Security
The countermeasures proposed by ENISA are organized into six main categories:
- Environmental Controls: These controls focus on the physical and digital environment in which the RIDP process takes place, aiming to minimize risks associated with factors such as lighting, backgrounds, distance, and camera quality, among others.
- Presentation Attack Detection (PAD) Controls: These measures concentrate on implementing advanced techniques for detecting attempts of biometric spoofing, such as texture analysis, motion analysis, reflectance analysis, and other indicators or liveness detection tests that prove the presence of a real person in front of a camera.
- Injection Attack Detection (IAD) Controls: Complementing PAD controls, these practices aim to identify attempts to inject false biometric data during live capture.
- Identity Document Controls: These measures focus on the verification and validation of identity documents presented during the RIDP process. Key practices include checking official document records, reading NFC chips (when available), and detecting alterations or forgeries.
- Procedural Controls: This set of practices addresses aspects related to workflow and user interactions during the remote identity verification process. Some key recommendations include requesting multiple pieces of evidence, conducting live sessions, and following standardized protocols.
- Organizational Controls: Finally, this group of best practices focuses on governance, policies, and processes at the organization level that provides the RIDP service. They include establishing clear roles and responsibilities, staff training, incident management, and continuous monitoring of emerging threats.
An important aspect highlighted is that, given the increasing sophistication of threats, it is no longer sufficient to rely solely on reactive or detection approaches. Instead, there is an emphasis on the need to implement preventive measures that hinder the success of attacks.
Some of the key practices mentioned include checking the status of identity documents in official records, reading NFC chips to validate holder information and the biometric photo, and the combined use of presentation and injection attack detection techniques.
| Control category | Key good practices |
| Environmental controls |
|
| PAD controls |
|
| IAD controls |
|
| Document controls |
|
| Procedural controls |
|
| Organisational controls |
|
However, the report also highlights certain challenges in implementing some of these practices. For example, the lack of centralized and updated records of identity documents at the EU level, and regulatory inconsistencies regarding the reading of NFC chips by private entities (trusted service providers and RIDP).
These obstacles reflect broader concerns related to the fragmentation of the regulatory framework among the Member States, which can affect the safe and consistent adoption of remote identity verification methods across Europe.
In summary, this set of best practices, organized into different control areas, aims to strengthen both the trust and reliability of remote identity verification services. Additionally, relevant challenges are identified that go beyond technical aspects and need to be addressed comprehensively.
Challenges and additional considerations
One of the key concerns that can affect the adoption of remote identity verification mechanisms is the inconsistency and fragmentation of the regulatory framework among the European Union Member States regarding the recognition and acceptance of RIDP. This results in differences in the levels of security that can be achieved, complicating interoperability and mutual trust among Member States.
José Luis Huertas (CEO, Mobbeel)
Another key aspect highlighted is the necessity for enhanced collaboration and coordination at the European level to comprehensively address security and trust challenges surrounding remote identity verification. This entails:
- Developing common standards,
- Sharing best practices, and
- Establishing harmonized oversight and compliance mechanisms.
Overall, the report concludes that while significant progress has been made, there still exist notable challenges related to the regulatory framework, alignment among Member States, and the imperative for greater collaboration at the European level.
Contact us if you want to learn more about how our technology can enhance passenger flows in airports.

I’m a Software Engineer with a passion for Marketing, Communication, and helping companies expand internationally—areas I’m currently focused on as CMO at Mobbeel. I’m a mix of many things, some good, some not so much… perfectly imperfect.

GUIDE
Identify your users through their face
In this analogue-digital duality, one of the processes that remains essential for ensuring security is identity verification through facial recognition. The face, being the mirror of the soul, provides a unique defence against fraud, adding reliability to the identification process.