“Any sufficiently advanced technology is indistinguishable from magic”.
This well-known aphorism by Arthur C. Clarke remains a perfect framework for understanding the perception of biometrics and verification technologies.
For decades, TV shows and movies have portrayed systems that instantly identify people, creating an aura of fascination around these solutions. However, what once seemed like pure science fiction is now part of our daily lives: we unlock phones with fingerprints, confirm transactions with our voice, and open bank accounts with a selfie.
The question is no longer “Is this possible?” but rather “How does this technology actually work?”
How do biometric identification technologies work?
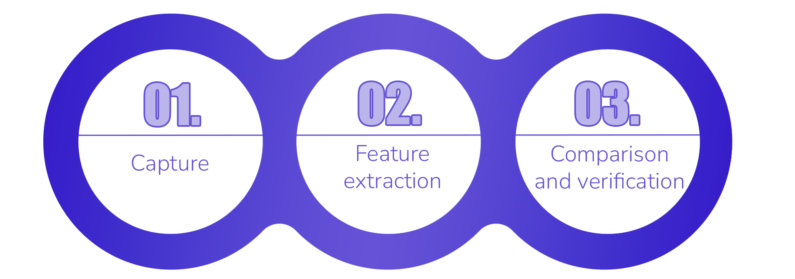
![]() Once any of the biometric traits described above have been captured with an electronic device (a camera, a microphone, a fingerprint sensor…) it is possible to extract a sort of features that best represent each of them.
Once any of the biometric traits described above have been captured with an electronic device (a camera, a microphone, a fingerprint sensor…) it is possible to extract a sort of features that best represent each of them.
Technological evolution
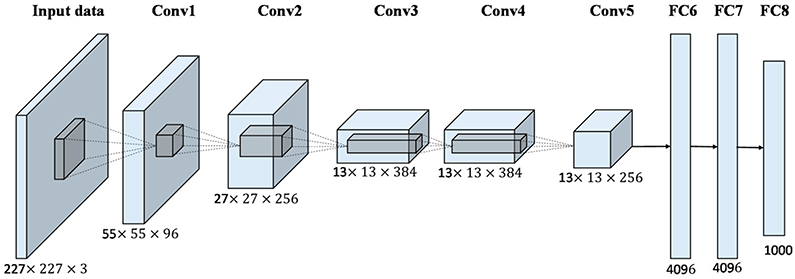
This approach enables end-to-end training, improving the performance of feature extractors by making them more robust.
![]() The access to large databases available on the Internet and the cheapening and improvement of hardware for intensive computing (GPUs) brought back to the fore the neural network architectures that had previously given discrete results.
The access to large databases available on the Internet and the cheapening and improvement of hardware for intensive computing (GPUs) brought back to the fore the neural network architectures that had previously given discrete results.
How to protect biometric data
The widespread use of biometrics raises critical questions about privacy and data protection. Unlike passwords or PINs, biometric data is immutable; we cannot change our fingerprints or face if they are compromised. This makes them an attractive target for cybercriminals.
To mitigate these risks, biometric technology manufacturers actively work on solutions to provide the highest degree of security in operations:
- Physical and logical security in biometric data storage: Storing biometric data requires a combination of physical and logical measures to prevent unauthorized access. From a physical perspective, these databases must be housed in facilities with security certifications such as ISO 27001.
- Advanced encryption for data protection: Biometric data, being unique and irreplaceable, requires robust encryption to prevent reverse engineering. Techniques such as homomorphic encryption allow computations to be performed directly on encrypted data, eliminating the need to decrypt it and minimizing exposure risk. Alternatively, cryptobiometrics integrates biometric features with cryptography to ensure templates cannot be reconstructed or used outside the original system.
- Zero-knowledge proofs: These techniques allow the authenticity of an identity to be verified without fully revealing it. This is a particularly interesting approach that aligns with regulations aimed at addressing concerns about the privacy of personal data.
Legal and ethical framework in biometrics
The implementation of biometric systems is subject to strict regulations, such as the General Data Protection Regulation (GDPR) and the new Artificial Intelligence Act (AI Act) in Europe. These regulations not only govern consent, storage, and use of biometric data but also address the risks associated with the use of AI-based technologies, including biometric applications. They ensure that companies managing biometric data adopt appropriate measures to protect privacy and prevent potential abuse while guaranteeing that AI systems are fair, transparent, and explainable. Specifically, the principles of proportionality in use and purpose, transparency in the use of these systems, and explicit user consent must be upheld.
Beyond regulatory aspects, it is essential to address biases in biometric algorithms, a growing concern in the development of AI-based technologies. Studies, such as those conducted by the NIST (National Institute of Standards and Technology), have shown that facial recognition systems, for example, may exhibit higher error rates for people of certain ethnicities, genders, or physical characteristics that are underrepresented in the training data.

The NIST report on demographic biases in biometrics and facial recognition technologies, which analyzes various databases and algorithms, showed that systems can be prone to significant errors when not trained with adequately diverse data. In this regard, it is crucial to train models with databases that are as diverse and representative as possible, reflecting the heterogeneity of the global population, in order to reduce the risk of biases and improve the system’s fairness and accuracy.
At Mobbeel, we are aware that biometrics is as powerful as a magic wand. That is why we continue to explore new possibilities with the goal of offering solutions that are not only at the forefront of innovation but also ensure maximum security and respect for our users’ privacy.
Let the magic continue!

I am Head of Mobbeel’s Innovation Department and I work together with the rest of the team in the research and development of biometric and identity verification technologies for the continuous improvement of our products.

GUIDE
Identify your users through their face
In this analogue-digital duality, one of the processes that remains essential for ensuring security is identity verification through facial recognition. The face, being the mirror of the soul, provides a unique defence against fraud, adding reliability to the identification process.