We all want the technology we use for onboarding new customers in our businesses to be as simple as possible, while still being the most secure in the world.
It makes sense, but we need to recognise that, although this is the main goal for companies that develop these types of solutions, it’s often very difficult to strike the right balance between two seemingly opposing forces: usability and security.
Today, we’re going to look at the factors to consider when analysing these variables (usability or user experience versus security) in a remote identity verification project. In most cases, it’s the client who needs to make decisions about configuring the technology, depending on their specific use case, the sensitivity of the data, applicable regulations in their sector, and so on.
Not all applications require the same level of security. Businesses want to offer users simple verification processes, but at the same time, they need to ensure these processes are robust enough to prevent fraud or identity theft.
What do we mean by usability in an identity verification process?
Usability, or user experience in the context of online identity verification, refers to how intuitive and easy it is for people to identify themselves when signing up to a platform.
To make the process simple, users need guidance with clear instructions so they can complete it quickly and without errors.
When we say that the registration process needs to be intuitive, we mean that someone with no advanced technical knowledge and who has never used the application before should be able to register without any issues. The steps should be straightforward and easy to follow.

It’s important to remember that the challenge with digital onboarding processes is that they’re usually only done once, and at a time when the customer hasn’t yet interacted with the company’s applications or systems.
Friction when using identity validation applications
You always need to put yourself in the shoes of your customer — the end user who’s going to use the application. The more steps and actions we ask them to take, the more obstacles we put in their way, making it harder for them to reach their goal of completing the registration process.
Barriers like complicated forms, multiple screens, and the need to remember complex passwords create friction, which can drastically lower conversion rates.
Additionally, when the technology isn’t up to scratch or the tools aren’t properly calibrated, the system might fail to capture either the identity documents or the user’s face correctly. This often means the user has to repeat the process, causing frustration.
Is it possible to reduce UX friction while maintaining security in identity verification processes?
Fewer steps, better user experience
A basic principle in any digital process is that the more steps required, the higher the risk of users abandoning the process. In digital identity verification, it’s crucial to minimise the actions required from the user without compromising security.
Optimising the process can be achieved by using technologies like OCR (Optical Character Recognition) for automatic data extraction and simplifying forms. This means users don’t have to manually input all the information from their documents, as the system can capture it directly from an image. By removing unnecessary fields and automating steps, the user experience is significantly improved.
This approach helps reduce friction, leading to higher conversion rates, without compromising security, as the removed steps don’t affect the biometric or document verification process.
Biometrics enhance usability compared to passwords
Passwords have long been a standard security measure, but they come with significant usability issues.
People tend to forget passwords, reuse them, or create combinations that are easy to guess, compromising both security and the user experience.
Biometrics make it easier to replace complex passwords and security questions with solutions like facial recognition or voice biometrics. With these methods, users don’t need to remember anything, eliminating the cognitive burden of managing multiple passwords.
Unlike passwords, which can be stolen or guessed, biometric data is unique to each individual, significantly improving security.
Guiding the user with interactive prompts
Another key aspect of improving the user experience is the interaction with technology during the verification process. Many users may not be familiar with the steps required to complete identity verification using document scanning and facial biometrics, so guiding them with clear, real-time prompts is essential.
- Step-by-step instructions: Providing clear guidance during the process, such as “Make sure your document is well-lit” or “Keep your head still while taking the selfie”, reduces errors and increases the likelihood of success on the first try.
- Immediate feedback: By offering real-time interactive messages, users can correct mistakes as they go (for example, if the document photo isn’t clear, there’s a reflection, or the angle is wrong), preventing them from having to start the process over again.
![]()
Mobbeel’s solution analyses different frames in real-time, providing feedback to guide the user until it automatically detects the expected document and captures it.
Additionally, during the capture stage, quality controls are applied to inform the user if the capture is being performed under suitable lighting conditions, whether the distance from the detection frame is correct, if there are strong glares or reflections on the document, or if, for instance, the user is trying to capture the back of the document when the front was requested, and vice versa.
Automatic document and selfie capture
One of the most effective features for improving the user experience is automatic document and selfie capture. Instead of relying on the user to handle the process, the technology itself automatically detects when the conditions are optimal for capturing the image. This minimises human error and reduces the number of failed attempts.
By removing the need for users to manually take photos, we ensure that the system captures the best possible quality image (both of the identity document and the person’s face), as the technology can automatically detect the right moment to take a well-focused, well-lit image.
Passive liveness detection
Unlike active methods that require user participation, such as moving their head from side to side, passive liveness detection works without any interaction. Users simply position their face in the centre of the oval.
This removes any friction from the process, improving the user experience without compromising security.
Enhanced usability with cross-platform solutions
Today’s users are omnichannel and expect to complete onboarding from any device, whether it’s a mobile, tablet, or desktop computer.
Identity verification solutions that allow for cross-platform interoperability not only improve usability but also increase success rates by offering greater flexibility to the user.
![]()
A good example of usability in identity verification is the digital onboarding process offered by MobbScan. This system allows users to scan documents and perform liveness checks with minimal intervention.
The system is designed to guide the user through each step, such as capturing identity documents, ensuring that the images are of high quality and captured correctly. This eliminates the need for users to repeat actions, not only improving the experience but also speeding up the verification process.
Security of identity verification solutions
Security of internal systems and processes
A fundamental certification to ensure the security of a provider’s verification systems is ISO 27001 for information security management.
Mobbeel is ISO 27001 certified. All information stored by our cloud-based products uses encryption mechanisms provided by the storage systems employed, at both the file and database levels, as well as for backups.
Additionally, our digital onboarding solution is approved and included in the Catalogue of ICT Security Products and Services (CPSTIC), meeting the high security requirements set by the National Cryptologic Centre (CCN).
The tests conducted to be included in the catalogue cover everything from forged identity documents to attacks on facial recognition systems (including screens, videos, hyper-realistic masks, professional makeup, deepfakes, etc.). All these tests are outlined by the CCN in Technical Instruction IT-14 for the certification of the Biometric Evaluation Module (MEB).
Advanced biometrics as the cornerstone of security
Biometrics not only verify identity reliably but also reduce dependence on passwords and security codes—both of which are more vulnerable to attacks like phishing—by linking verification to unique features such as biometric patterns.
Biometric technologies, such as facial recognition, voice, or signature verification, play a crucial role in protecting user identity. Biometrics provide a unique, non-transferable method of authentication, as physical or behavioural traits cannot be easily replicated.
Accuracy, reliability, and bias
Mobbeel’s biometric engines are trained using artificial intelligence to improve accuracy and reduce bias.
We adhere to the NIST standard for facial recognition algorithm evaluation, ensuring fairness in assessment and working to prevent biases related to race, age, and gender.
Evaluations conducted by the NIST’s Face Recognition Vendor Test (FRVT) (1:1 and 1) demonstrate that Mobbeel’s systems have a high degree of accuracy and reliability in facial recognition processes.
Spoofing detection
Liveness detection is a security mechanism that ensures the person involved in the verification process is physically in front of the device, rather than being a photo or pre-recorded video. This technology is essential for combating presentation attacks (spoofing), where fraudsters attempt to deceive the system using images or videos of someone else.
There are two types of liveness detection:
- Active liveness detection: Requires the user to perform certain actions, such as moving their head or blinking, to prove they are physically present.
- Passive liveness detection: Requires no user interaction, as the system automatically detects if the person is alive by analysing biometric signals such as subtle eye movements or blood flow.
Document verification and fraud detection
In addition to biometric authentication, a robust identity verification process must include document validation to ensure the documents are genuine and have not been tampered with. Technologies like OCR and data extraction via NFC (for documents with embedded chips) allow the system to verify the authenticity of identity documents and detect any alterations.
Additionally, advanced solutions like MobbScan incorporate fraud detection techniques that analyse both the content and appearance of the document (verifying the integrity of QR codes, typography, and potential manipulation of the facial image).
with international regulations and standards
Global regulatory frameworks, such as PSD3 for financial transactions or eIDAS 2 in the European Union, require that verification processes meet specific security requirements. These regulations ensure that electronic transactions and identity verification are conducted securely, minimising the risk of fraud.
Adhering to these standards is essential for companies operating in critical sectors such as finance and banking, where security requirements are more stringent.

![]()
MobbScan includes a Presentation Attack Detection (PAD) module that implements countermeasures against the following Presentation Attack Instruments (PAI):
- Printed images
- Paper, silicone, or latex masks
- Screen captures or images
- Video recordings
- Characterisation or makeup
- Deepfakes
- Video injections
Balancing user experience and security to prevent fraud
Conversion rates, whether for automatic approvals or rejections, are influenced by various factors, including the specific details of the project, the client’s industry, and the regulations of the country where the solution is deployed.
In our case, we also allow different business rules and customisations to be configured through a validation matrix. This matrix sets the rules and thresholds that dictate when an identity verification or user registration process will be approved, rejected, or sent for manual review.
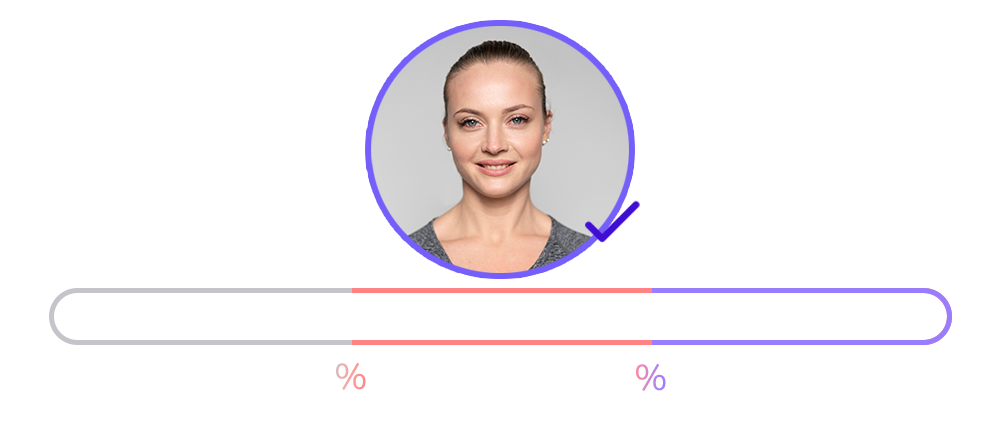
For automatic decisions, the technology relies on biometric comparison (matching the user’s selfie with their ID photo) and liveness detection (confirming that the person is physically present and not a spoofing attempt). These systems operate with configurable thresholds:
- Above the upper threshold: If the biometric match score or liveness score exceeds a certain value, the system automatically approves the user.
- Below the lower threshold: If the scores fall below a minimum level, the system automatically rejects the user.
- In-between (grey zone): If the scores fall between these two thresholds, the system cannot make a clear decision, and the process is escalated for manual review by an agent.
This system offers great flexibility, but companies need to strike a balance between usability and security.
If the thresholds are set too high, the system will become overly strict, leading to a high rate of false positives (genuine users being flagged for manual review).
On the other hand, if the thresholds are too relaxed, while more users will be automatically approved, the risk of fraud increases due to the acceptance of illegitimate users.
This balance is crucial when configuring a remote identity verification system, but it will never be the same for two different companies, as each will have its own unique requirements (sector, regulations, customer base, workflows, channels, etc.).
![]()
On average, with Mobbeel’s technology, approval rates vary depending on how strict or flexible the processes are configured.
For instance, if we consider multiple attempts per user, the approval rate can reach up to 99%, as users who initially fail often succeed on a second attempt.
Conclusions
Mobbeel is a technology company that offers a wide range of solutions and technologies, providing clients with the flexibility and modularity needed to strike a balance between delivering seamless user experiences and safeguarding against identity fraud.
With advanced technologies such as facial biometrics, passive liveness detection, and automatic document capture, the onboarding process is optimised, ensuring high accuracy and compliance with international regulations like eIDAS and PSD3.
Finding solutions that deliver a great user experience without sacrificing security is essential for businesses that don’t want to see their conversion rates suffer during the onboarding process.
Are you having issues with the usability of your applications?
Are your customer conversion rates too low during onboarding?
What are you waiting for? Get in touch with us—we’re here to help!
Contact us if you want to find out how we can help you find a balance between security and usability.

I’m a Software Engineer with a passion for Marketing, Communication, and helping companies expand internationally—areas I’m currently focused on as CMO at Mobbeel. I’m a mix of many things, some good, some not so much… perfectly imperfect.

COURSE
The first COURSE on Digital Onboarding
Understanding the technology before implementing it ensures that you make the most of its potential and make informed decisions that benefit both your company and your end users.
We have developed a course that brings together everything you need to know about digital onboarding. This technology is the first point of contact with your customer and defines the course of your relationship.





