FIDO2 is the acronym for Fast Identity Online and allows users to use their own devices (smartphones or laptops with biometrics, USB security keys, etc.) to authenticate themselves on online services in mobile and desktop environments.
FIDO is a technical specification promoted by the FIDO Alliance, a consortium of technology, financial, and government companies. This consortium was created with the aim of eliminating the use of passwords on websites and applications, and improving authentication processes.
By eliminating the need for passwords, the FIDO2 standard enhances security, convenience, and protection against fraud in digital interactions, providing users a more reliable and modern authentication experience.
FIDO2 is the evolution of FIDO and enables authentication to be done in web environments as well.
Download our guide about the FIDO2 Standard
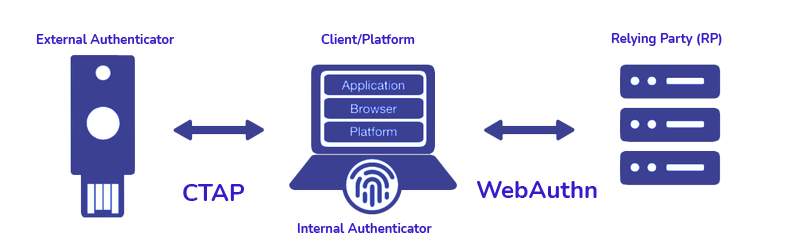
FIDO2 Specification Protocols
The FIDO2 specification is divided into two different protocols:
- The W3C WebAuthn protocol, which defines the communication between the browser (user agent) and the FIDO2 server (relying party).
- The FIDO Alliance CTAP (Client-to-Authenticator Protocol) which defines the communication between the browser (user agent) and the device that authenticates the user (authenticator)La especificación FIDO2 se divide en realidad en dos protocolos distintos:
What is FIDO2 used for?
Defining what is FIDO2 used for is easy since it enables us to use the biometrics that we have stored on our computer or mobile device (fingerprint reader, Touch ID, FACE ID, an external token, etc.) to access any website or application.
Authentication would be done locally, on a previously registered device, using biometrics as the second factor of a two-factor authentication process. In short, it would make the user’s life easier because they do not have to memorise their username and password.
In this way, the security of the process is reinforced and the user has a more usable access mechanism to the platform
How does FIDO2 work?
At a high level, there are two main flows or operations in FIDO2:
Registration operation in FIDO2
The user registers with an online service and generates a new key pair on the device, consisting of a private key and a public FIDO2 key.
While the private key is stored on the device and is only known on the client-side, the public key is recorded in the web service’s key database.
The flow steps are:
- The user logs in to the company’s web platform from his smartphone or laptop and authenticates with traditional credentials (username/password) to prove his identity.
- In any part of the website (user profile, configuration, etc.) we will find the option to enable the biometric login from that device.
- When selecting this option, the exchange of cryptographic keys takes place, which will allow the same device to be used later to authenticate the user.
The authentication process in FIDO2
Subsequent authentications are only possible if the private key is provided, which must be unlocked by a user action:
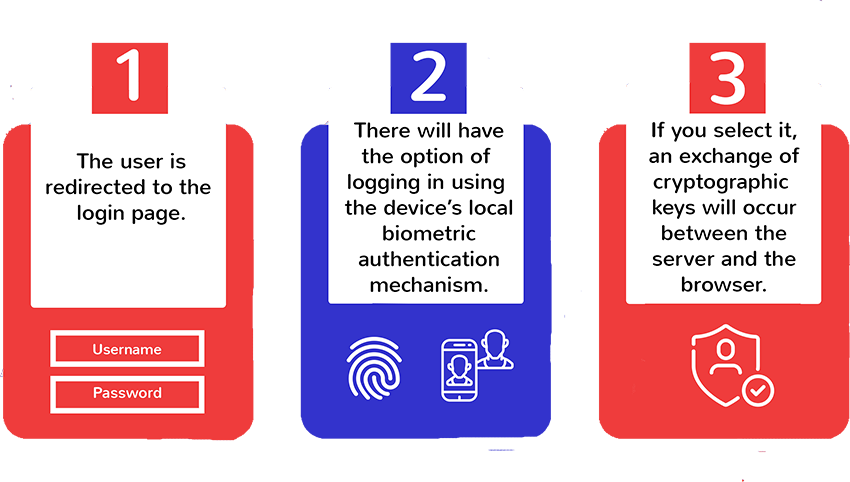
- The unauthenticated user visits the company website from a mobile or desktop browser and is redirected to the login page.
- On the login page, in addition to the traditional username/password option, you will have the option of logging in using the device’s local biometric authentication mechanism.
- If that user/device was previously registered, an exchange of cryptographic keys would occur between the server and the browser. This exchange will allow the user to be authenticated through the local mechanism of your choice (TouchID or FaceID on an iPhone, TouchID on a Mac, fingerprint, face or iris sensors on an Android and so forth).
Out-of-band authentication in FIDO2
There is also the possibility of performing out-of-band authentication. The user will receive the authentication request through an SMS link to the phone number with which they have registered and completed the authentication on the mobile device itself.
In this way, OTP messages used in the financial industry as a second authentication factor can be replaced by secure messages that request user authentication through the biometrics of their own device.
Benefits of using the FIDO2 Standard
The key advantages of using the FIDO2 Standard are:
- Security: FIDO2 encrypts the login by default with a pair of keys (private and public) that can only be unlocked with the registered device. The cryptographic login credentials are unique for each website. Besides, they never leave the user’s device and they are not stored on any server. This security model prevents risks of phishing, password theft or replay attacks.
- Convenience: Users unlock their cryptographic credentials with the security methods built into their devices (fingerprint sensors, facial recognition, etc.), USB keys, Bluetooth bracelets, etc.
- Privacy: Cryptographic keys are unique for each website, so they cannot be used to track the user between different sites. In addition, biometric data never leaves the user’s device. It solves problems that could arise from centralised storage of biometric fingerprints of users.
- Scalability: The decentralised authentication model allows high scalability. Web applications perform authentication using a standardised Javascript API supported by most modern browsers.
FIDO2 Powered by Mobbeel
Our multibiometric recognition solution, MobbID, supports the FIDO2 Standard to respond to multiple use cases, such as:
- Scenarios in which a double authentication factor (2FA) is required, such as those needed after the appearance of PSD2, the European directive to reinforce the security of banking operations carried out on the Internet.
- Access to web environments without the use of passwords.
- The substitution of OTP codes.
In addition, together with Telefónica Tech’s Identity Innovation Laboratory, we have developed a solution based on the FIDO2 Identity standard. It allows transactions to be confirmed through secure SMS and biometrics, helping to prevent SIM Swapping fraud.
If you are looking for an authentication system through the FIDO2 Standard, do not hesitate to contact us!

I’m a Software Engineer with a passion for Marketing, Communication, and helping companies expand internationally—areas I’m currently focused on as CMO at Mobbeel. I’m a mix of many things, some good, some not so much… perfectly imperfect.

GUIDE
Identify your users through their face
In this analogue-digital duality, one of the processes that remains essential for ensuring security is identity verification through facial recognition. The face, being the mirror of the soul, provides a unique defence against fraud, adding reliability to the identification process.