Liveness detection is a cutting-edge technology that ensures the authenticity and veracity of an individual in a digital environment. By using advanced algorithms and techniques, liveness detection distinguishes between a live person and an attempted fraud.
This innovative solution provides an additional layer of security in processes such as digital onboarding, ensuring the integrity of processes and trust in the digital world.
Nevertheless, one of the main obstacles facing biometric recognition systems is impersonation attacks. With liveness detection, companies can confidently protect against impersonation and ensure a seamless user experience.
In the middle of this growing fraud scenario, liveness detection is vital to ensure the security of biometric-based verification processes.
A look at the history of liveness detection
In 1950, renowned mathematician and computer scientist Alan Turing developed the famous Turing Test, a noteworthy milestone in the history of artificial intelligence. This test was designed to assess the ability of a computer to show intelligent human-like behaviour.
The idea behind the Turing Test was that if a machine could perform a talk convincingly enough to fool a human judge into believing it was interacting with another human being rather than a machine, then the machine could be considered human-like intelligence.

The Turing Test became a significant benchmark in artificial intelligence and stimulated the development of algorithms and systems capable of simulating human behaviour. Nevertheless, as technology advanced, it became clear that the Turing Test did not fully address the question of the authenticity of the interaction between a computer and a human.
When it was concluded, the concept of liveness detection came into play. Unlike the Turing Test, which assesses a machine’s ability to mimic human behaviour, liveness detection uses artificial intelligence algorithms to determine if a computer interacts with a real person rather than a simulation.
A pioneering view of liveness
Dorothy E. Denning became famous after Tuning when in 2001 published an article entitled “It’s “liveness,” not secrecy, that counts” in Information Security magazine. Denning introduced the term liveness in the context of biometric authentication. Rather than focusing only on protecting secrecy, Denning argued that a good biometric system should not rely only on keeping the biometric information used for authentication secret.
Furthermore, she emphasised that the validation process should focus on verifying the liveness, i.e. ensuring that the sample came from a live person and not a fraud.
Denning’s view was revolutionary for its time. At a time when most biometric authentication systems focused on protecting the secrecy and privacy of biometric data, Denning understood the importance of liveness detection as a critical element of ensuring authenticity and security.
Her perspective laid the foundation for creating more secure and reliable identity protection and fraud prevention systems.
But then, what is liveness detection?
Liveness detection is the ability of a system to determine the authenticity of a face, voice or other biometric feature. In other words, the technique verifies if the characteristic presented to the camera in a verification process comes from a real person or is an artefact.
Therefore, the liveness technique confirms the authenticity of the individual performing the process and identifies spoofing attacks (presentation attacks).
Liveness detection uses advanced algorithms and machine learning models to analyse and process the captured information. These algorithms identify specific patterns and features that indicate the sample authenticity, enabling accurate and reliable detection.
What is the difference between facial recognition and liveness detection?
Firstly, we need to say that they are not the same.
The main difference is that facial recognition answers “Are they the right users” whereas liveness answers the question “Are they real individuals?”.
Both terms are connected and can work together, but they are different. Liveness only involves detecting a human face in a frame or video, not identifying the person. On the contrary, facial recognition goes beyond simple liveness detection, trying to determine who the person is in a verification or authentication process. In this sense:
- In facial verification, a capture of the identity document is made, and the technology takes the user’s selfie to compare the photo on the ID card with the selfie, confirming that the individual is who they claim to be. Facial verification is normally used for onboarding processes or remote incorporation processes.
- Facial authentication compares the biometric data of a user’s previously registered with a selfie taken at that moment. In this case, the aim is to confirm the user’s identity to access an account or authorise a transaction.
How does liveness detection work?
As commented, liveness is responsible for determining if the captured biometric data is real or being imitated to gain unauthorised access to the biometric system.
Liveness works differently depending on whether an image or video is analysed.
When an image is analysed in the liveness process:
- The individual presents a biometric sample in front of the camera.
- After that, the image is processed and ready for feature extraction. The output biometric template of the feature extraction process is a distinguishable sample of distinct features that allows the classifier to decide if the sample is real or fake with the help of pre-trained data. Genuine samples are processed for identification, while fake ones are automatically discarded.
When a micro video is analysed in the liveness process:
- The user presents a biometric sample in front of the camera.
- Then, the technology records a micro video from which a series of images are extracted, and predictions are made about each of them, with the neural network architectures making their own decisions (deep learning end to end).
- The technology identifies if the user is a real person or an impostor.

In both cases, the purpose of liveness is to determine if the biometric sample presented is real or fake. If the sample is fake, it calls an impersonation or presentation attack.
Presentation attack detection (PAD)
Presentation attacks (PA), or impersonation attacks, are purely biometric vulnerabilities not shared by other security solutions and require specific measures.
According to ISO/IEC 30107-1, the biometric feature used in an attack is a presentation attack instrument (PAI).
In these attacks, fraudsters use an artefact or instrument, usually artificial, such as a 2D facial impression, a video or a realistic 3D mask to gain access to the biometric system fraudulently.
Let’s review the most common classification:
Photo attacks
In this kind of attack, a photo of the impersonated identity is displayed in front of the camera.
The photo can be printed or can be displayed on a screen. In the latter case, the attack is performed on a device’s screen, such as a mobile or tablet.
This type of attack also includes another more complex technique, photo masks. In this case, the instrument is a photo of the legitimate user with holes in the mouth, eyes and nose.
Video attacks
In In this attack, the artefact presented to the sensor of the biometric recognition system is a video played on a mobile phone, tablet or laptop.
They are also known as replay attacks.
Mask attacks
In mask attacks, a 3D reconstruction of the face of the person to be impersonated is made.
The mask can be done in various ways. The most common are:
- Printing a photo of the genuine user and glueing it onto a deformable structure such as a plastic bag.
- Print a frontal and side photo of the legitimate user and generate a 3D model.
- Take a 3D capture of the attacked person.

If you are interested in learning more about other attacks, such as synthetic theft and the famous deepfakes, you can read our article, Deepfakes: how to guarantee authenticity?
Liveness detection types
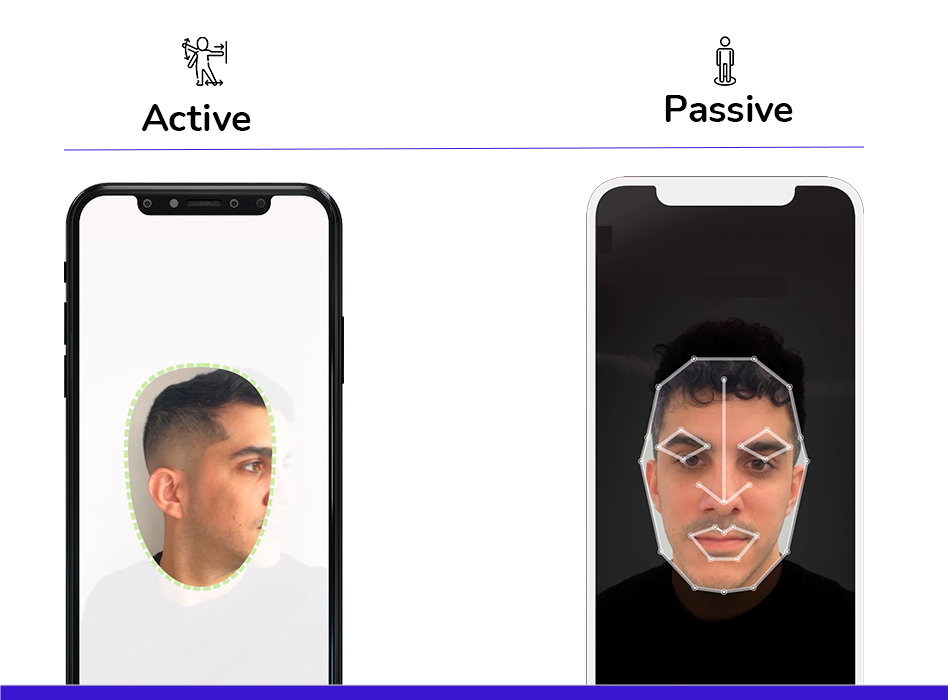
Active liveness detection
Active liveness detection involves user collaboration to verify the authenticity of a facial sample in real time. This technique uses physical actions performed by the user to confirm that the sample is from a genuine person and not a static image, mask or pre-recorded video.
Some common methods used in active liveness detection include:
- Motion analysis: A flat object moves differently than a real face. This method includes the calculation of information about points in an image. The method is based on focus distance analysis, optical flow-based analysis and analysis based on scenic cues.
- Involuntary action recognition: Detection of random and unpredictable user actions, such as winks, which are difficult to replicate with a static image or pre-recorded video.
- Blink pattern analysis: Natural blink patterns can be analysed to detect the presence of a real person. For instance, missing or irregular blinking patterns could indicate a fake image.
There are other methods, such as 3D properties, that are not widely used but fall under this type of indicator.
Passive liveness detection
Passive liveness detection is based on analysing visual and biometric features in the facial image without requiring the user’s collaboration. This technique uses algorithms and machine learning models to identify signals that indicate the authenticity of the sample. It occurs when the technology takes a selfie of the user
Some common methods used in passive liveness detection include:
- Texture analysis: A fake face produces a different texture pattern than a genuine one. Textural features are extracted from the face image to provide detectable information to help distinguish real identities from fake ones. For example, differences in skin texture.
- Depth detection: Image depth information is used to verify if the sample is three-dimensional and not a flat or printed image.
- Background motion analysis: The environment or background is observed to detect abnormal motion signals that may indicate an attack.
- Micro video capture from which a series of images are extracted.
Challenges in liveness detection
Adversarial attacks
Sophisticated adversaries constantly devise new methods to bypass liveness detection. Adversarial attacks involve crafting specifically designed samples to deceive the system, necessitating ongoing refinement of detection algorithms to stay ahead of these challenges.
Variability in capture conditions
Liveness detection accuracy can be affected by diverse environmental factors such as lighting conditions, angle variations, and device quality.
User experience
Balancing security with user convenience poses a challenge. Implementing stringent liveness detection without causing inconvenience to users during authentication processes requires thoughtful design and optimisation.
Regulatory compliance
Compliance with evolving regulatory standards, such as ISO/IEC 30107, ensures that liveness detection systems meet industry-specific security requirements, providing a benchmark for effective implementation.
Mobbeel facial liveness detection features
Our facial liveness detection technology safeguards digital identities, complying with the stringent standards outlined in ISO/IEC 30107. Our commitment to these standards reflects our dedication to providing robust, trustworthy security measures.
Versatility in methodology: active and passive liveness
Mobbeel’s liveness detection offers two distinctive methodologies:
- Active liveness detection: this method engages users in real-time actions to validate the authenticity of facial samples. Incorporating user participation, such as specific gestures or movements, confirms the presence of a live person, preventing the acceptance of static images or recorded videos as commented.
- Passive liveness detection: in contrast, passive one operates without direct user collaboration. This method uses cutting-edge algorithms and machine learning models to identify subtle features indicating the presence of a real person.
Advanced AI defence against presentation attacks
Our system harnesses the power of artificial intelligence to face impersonation attacks meticulously. It intelligently distinguishes and deflects attempted breaches from various presentation attack instruments, preventing unauthorised access to sensitive systems. It is important to mention that NIST has assessed the accuracy of our algorithms, testing the resistance to spoofing attacks.
Well-balanced security and usability
We prioritise usability with stringent security measures, designing seamless and intuitive authentication processes.
Versatility for customised solutions
Mobbeel’s facial liveness detection offers versatility in implementation, catering to diverse needs and system configurations. Our solution adapts to varying environments, whether integrated into mobile apps, gateway, or other platforms, ensuring consistent and reliable performance across different applications.
![]() We highly recommend passive liveness detection over active one since it reduces friction and increases the process completion rate by not requiring the user’s active collaboration. Furthermore, it is an imperceptible step for the user, so fraudsters do not know when it occurs.
We highly recommend passive liveness detection over active one since it reduces friction and increases the process completion rate by not requiring the user’s active collaboration. Furthermore, it is an imperceptible step for the user, so fraudsters do not know when it occurs.
Use cases where include liveness detection
KYC digital onboarding with liveness detection
Facial liveness detection can verify that a user is genuine and prevent the creation of fraudulent accounts during the registration or onboarding process. Furthermore, once the technology proves the user is real, their biometric template can be stored for forthcoming authentications.
Biometric authentication with liveness detection
Facial liveness techniques can be used as an additional layer of security in authentication systems.
In terms of authentication, the possibilities are endless. Some examples where liveness can be applied are:
- User action confirmations such as transactions or account deletion: requiring users to make specific facial movements during the transaction reduces the risk of a fraudster using a photo or video to impersonate the user’s identity.
- Physical access control: security systems in buildings, facilities or wards can use facial liveness to allow access only to authorised individuals. It prevents photos or masks from being used to fool the system and ensures that only real people can enter.
- Multi-factor or two-factor authentication (2FA) for making payments.
- Password replacement.
Voice biometrics and liveness detection
Liveness detection also applies to voice authentication processes. In these processes, liveness determines whether the voice corresponds to a real individual’s voice or is an attack.
One of the most typical attacks is a replay attack, in which the voice of a legitimate person is recorded and then replayed to fool the biometric system. Nevertheless, these attacks can be detected with liveness, as they look for only specific features in an authentic voice in real time.
In addition to the replay attack, there are other presentation attacks, such as speech synthesis, where technology artificially generates a person’s voice. Despite using technology to create a voice, liveness techniques can detect the subtleties and differences between an artificially generated voice and a real voice.
The third type of attack is voice conversion, in which a person’s voice is taken and modified to sound like another person’s. Also, liveness can detect these manipulations and guarantee voice authenticity.
Feel free to reach out if you are interested in introducing anti-spoofing (liveness detection) techniques in your processes.

I am a curious mind with knowledge of laws, marketing, and business. A words alchemist, deeply in love with neuromarketing and copywriting, who helps Mobbeel to keep growing.

GUIDE
Identify your users through their face
In this analogue-digital duality, one of the processes that remains essential for ensuring security is identity verification through facial recognition. The face, being the mirror of the soul, provides a unique defence against fraud, adding reliability to the identification process.