In the digital age, our mobile devices increasingly connect our lives. Nevertheless, security risks are also rising with the increasing reliance on mobile technology. One of the emerging dangers is SIM swapping fraud. SIM swapping is a technique in which criminals gain unauthorised access to a user’s SIM card.
What is SIM Swapping? SIM Swapping meaning
SIM Swapping is a technique used by criminals to obtain a duplicate or clone of a SIM card linked with a phone number to impersonate the identity of the line holder and gain access to their bank accounts by sending an SMS (OTP code) used as a two-factor authentication.
In other words, criminals persuade or trick mobile phone providers into asking for a duplicate SIM card.
Once cybercriminals have access to the victim’s phone number, they can intercept communications and perform malicious movements, such as accessing their bank accounts, making unauthorised transactions via Bizum, or even impersonating the victim on social media.
This fraud has been widespread in recent years that the AEPD has imposed fines ranging from 70,000 euros to 3.94 million euros (5.8 million euros in total) on Spain’s leading operators (Vodafone, Orange, MásMóvil, Simyo, Telefónica, and Xfera) for not complying with data protection and not protecting the confidentiality and data of their customers enough. The Spanish agency points out that the companies did not apply adequate mechanisms to check the identity of the owner of the line when ordering a duplicate SIM.

This severe warning from the AEPD and the ease with which cybercriminals manage to perform SIM swapping or fraudulent duplicate SIMs push mobile carriers to reinforce their security, prevention, and identity verification measures.
How does SIM Swapping work? Steps
The SIM swapping process involves a series of steps fraudsters must carry out.
-
Personal data collection
The first step in obtaining a duplicate SIM card is to gather sensitive information from the current owner of the card. Some essential data are the phone number, email address, and DOB.
Cybercriminals usually acquire this data through social engineering techniques or attacks such as spoofing, phishing, smishing, pharming, or vishing.
A typical example used by a scammer that corresponds to a case of smishing is impersonating the victim’s bank through fraudulent SMS messages that appear real, usually referring to an account or payment issue. The message contains a link to a fraudulent landing page that resembles that of the bank where the theft of data (card number, credentials to access online banking, etc.) occurs.
Another widespread example of vishing is impersonating the customer service department of a service provider or the bank. Criminals first obtain confidential data from the victim by phishing. Once they have it, they use a fake caller ID and hide the real number from which they are calling to make the victim’s phone display the number of the company they claim to be calling from. Scammers sometimes claim that someone else has purchased with the victim’s debit card or transferred money using their account number. At that point, they ask the victim for a code they will receive by SMS to block the card, cancel the transfers, and provide other bank details.
-
Contacting the mobile phone provider
Once the fraudster has enough information, they contact the victim’s mobile phone provider pretending to be the victim.
They use manipulative tactics to convince the provider that they need to transfer the phone number to a new SIM card because they have lost their mobile phone.
Other times, they provide the mobile phone provider’s shop with a fake complaint that they have been the victim of mobile theft or a photocopy of the ID card with the owner’s photo changed to that of the cybercriminal.
-
Fake identity validation
Criminals may provide personal information about the victim, answer security questions or even use spoofing techniques to convince the agent in the shop or over the phone that they are the line’s owner.
-
Card cloning and SIM duplication
Once the phone provider is convinced, they transfer the victim’s phone number to the new SIM card. It is done by deactivating the original SIM card and activating the new one in a mobile phone in the hands of the scammer.
Once the cybercriminal has the new SIM card, they can receive calls, SMS, and OTP codes, using this information to access bank accounts, make transactions and commit other types of fraud.
One of the first telltale signs that this crime can be detected is that the SIM card owner’s mobile phone has no signal when the telephone operator deactivates the original SIM card and activates the cloned card.
Second-generation SIM Swapping with call and SMS forwarding
In these cases, the criminal diverts calls from the line the victim has not requested.
To activate the call forwarding, they call the phone operator’s customer service, who performs a security check in which they ask for some information that the criminal has previously gathered, such as name and surname, ID number, address, DOB, some bank account digits, contract number, etc.
In this call, the cybercriminal says that the SIM card has trouble receiving text messages and asks the agent to divert the calls to a different number.
Nevertheless, only with active call forwarding is it impossible to receive SMS. An additional setting needs to be activated to receive SMS.
This type of fraud is presented as the evolution of SIM Swapping or advanced SIM Swapping.
Current SMS problems and use two-factor authentication: PSD2
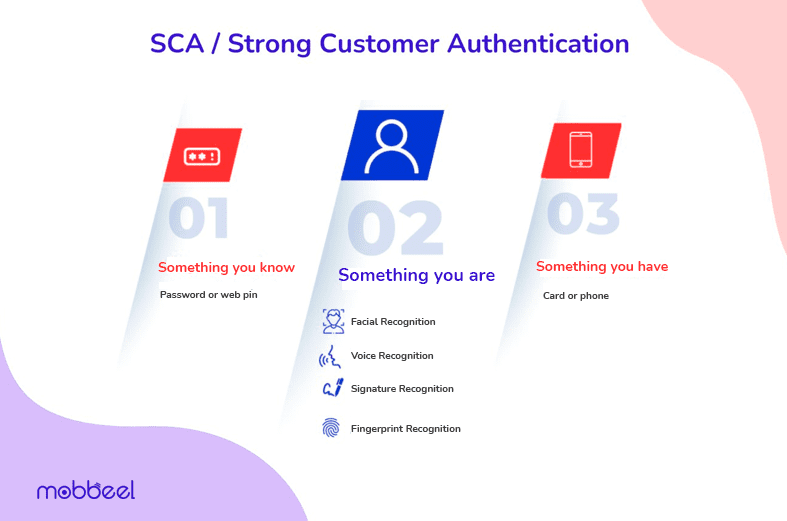
At the end of 2019, the PSD2 (Revised Payment Service Directive) came into effect in the European Union to strengthen the security of digital transactions and payments, imposing the use of at least 2-factor authentication (2FA) to verify the identity of users performing a banking transaction.
Strong Customer Authentication (SCA) requires at least 2 factors among the following:
- Something you know (password or pin),
- Something you have (card or mobile phone) and
- Something you are (biometric recognition),
in order to verify the identity of a person during a transaction…
Most banks have opted to use as a second authentication factor an SMS message with a one-time, time-limited code (OTP / One Time Password) and this presents the second security breach in the authentication processes in cases of SIM swapping: banks, insurers, and credit institutions.
Why are SMS for sending OTP codes not secure?
For banks to use SMS as 2FA is not secure because if the smartphone is stolen or the SIM card is duplicated, the SMS and therefore the code used as a second authentication factor to authorise a transaction would be accessible.
Usually, the confirmation code can be seen even when the screen is locked, so stealing the phone, even without knowing how to unlock it, would be enough to gain access to bank accounts.
From this point onwards, pray that the bank can analyse the behaviour of the account and detect if there is an impostor misusing the online banking application.
Then, how to avoid SIM Swapping fraud?
At this point, you will have realised that in order to prevent SIM swapping fraud, the problem must be approached on two different fronts:
- Strengthen telephone operators’ identity verification measures when registering SIM cards, requesting duplicate SIM cards and even requesting prepaid cards (we also prevent the use of these prepaid cards for terrorist purposes) and then using face recognition when applying for a SIM card duplicate.
- Use user biometrics as a second authentication factor within the financial industry.
Identity verification in the SIM card registration process
Mobile phone providers, remotely and in person, can use MobbScan, our technology, to verify identity while registering new SIM cards.
Mobbscan helps to detect an ID document’s veracity and confirm that the individual is its owner through biometric facial recognition.
The telephone operator LEBARA uses Mobbeel’s technology to verify identity for SIM card activation both in face-to-face and in online processes.
In both the document verification and facial verification steps, fraud detection measures are applied, including in the first case, verification of content, appearance, and image files, and in the second, liveness detection.
A third module can be added to reinforce the process. It involves unattended video identification for cases in which the process is carried out remotely, where the process is recorded, and a trained agent reviews it once it is completed to accept or reject it.
Identity verification in the SIM duplicate application process
The process would be similar to the SIM card registration process for a duplicate SIM application.
A new registration process would be performed to ensure that the identity of the person requesting a duplicate is the same as that of the old SIM card. In that sense, the technology using a mobile phone or tablet would capture the identity document, check its authenticity, and then take a selfie to compare the photo on the document with the selfie and validate that the individual presenting the document is who they claim to be.
In this way, we can prevent an impostor from duplicating a SIM card linked with a phone number that does not belong to them, as well as possible cases of fraud committed by agents in the shop.

Facial biometrics as a second authentication factor for banks
The fight against SIM Swapping is a task not only for telephone operators but also for banks.
Simple identification methods such as passwords or OTP codes are unsuitable for verification or authentication procedures requiring higher levels of security.
Many banks have started to ask their users to enter the Secure E-Commerce Code (CES) followed by the OTP code they receive by SMS to reinforce the process. Nevertheless, more is needed.
In this sense, biometrics appears as a component that cannot be stolen or falsified, or at least not as easily as in the abovementioned cases. For this, the user would be asked for the first authentication factor (password, for example.), and then the technology would take a selfie as the second authentication factor.
Another option, FIDO 2 and the use of biometrics as an authentication factor
To solve the problem generated by the use of SMS codes as a second authentication factor, we have jointly developed with Telefónica Tech’s Identity Innovation Lab a solution based on the FIDO2 Identity standard, which allows transactions to be confirmed through secure SMS and biometrics.
In this case, the SMS that is sent requests the user’s authentication through the biometrics of their own mobile device; TouchID, FaceID, or pattern or unlock code, making the process much more secure.
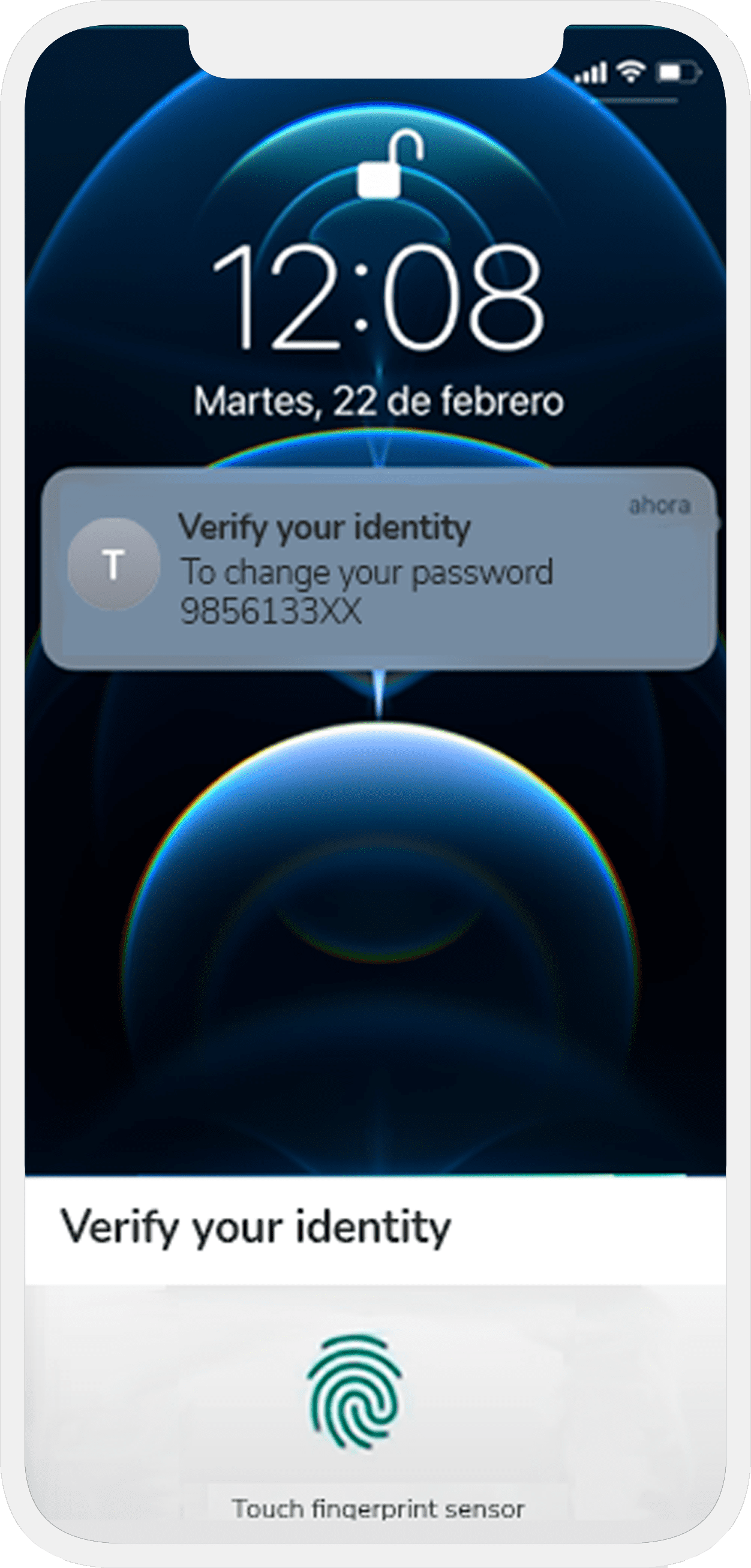
Sending this type of more secure SMS helps to prevent bank account access fraud.
Hence, at Mobbeel, we have the technology to help prevent this type of fraud by fighting against scammers on the mobile phone operators’ side and the banks’ side by implementing authentication solutions based on facial recognition or the FIDO2 Standard.
If you want to know more about our technology and how we can help you avoid SIM Swapping fraud or use biometrics as a second authentication method, don’t hesitate to contact us!

I’m a Software Engineer with a passion for Marketing, Communication, and helping companies expand internationally—areas I’m currently focused on as CMO at Mobbeel. I’m a mix of many things, some good, some not so much… perfectly imperfect.

GUIDE
Fight against the most popular fraud in telcos
SIM Swapping is a type of fraud in which a person obtains a duplicate SIM card linked to a phone line, impersonates the owner, and gains access to the customer’s bank accounts.




